Cyber Security Solutions
VPN
- Empower employees to work from anywhere, on laptops or personal mobile devices, at any time. Protect employees on or off the network. Enforce posture for connected endpoints.
Security Services Engine
- Create analytic policies by segment users, groups, and devices using information to create analytic policies.
Secured Endpoints
- Remediating any issues on endpoints that impact operational costs and detracts time from other customers.
- End users are working both in and out of the network with their devices.
- Encrypted threats are reaching endpoints unchecked.
Expert Security
- Focus on extended defenses powered by threat intelligence, expert guidance and knowledge transfer, empowering mature IT-security teams to face down complex threats and targeted attacks.
Identity management
- Essentially, this is a process of understanding the access every individual has in an organization.
Email Security
- Scan inbound and outbound messages with powerful anti-spam and anti-virus.
- Provide policy-enforced and on-demand email encryption
- Get up-to-date security with real-time threat intelligence Enable email data loss prevention & compliance Control costs with scalable and flexible deployments.
Network Analytics
- Analytics, you will always know who is on your network and what they are doing. solution that can detect malware in encrypted traffic and ensure policy compliance, without decryption.
Real-Time Antivirus
- Continuously scans your devices for viruses, worms, Trojans, cryptolockers, rootkits and spyware — online threats.
Application security
- Apps require constant updates and testing to ensure these programs are secure from attacks.
Security Solutions & Services
IITECH provides high-end secured end-to-end internet connectivity, securing our customers networks from vulnerabilities that can negatively impact clients assets on data confidentiality. It’s within our priority to provide security techniques to protect the corporates assets from outside of the network and inside. We are fully responsible for maintaining data assurance for any corporates and ensuring the data integrity and confidentiality of information. Managing and controlling risks. We implement tools and applying security techniques for mitigating both external and internal threats.
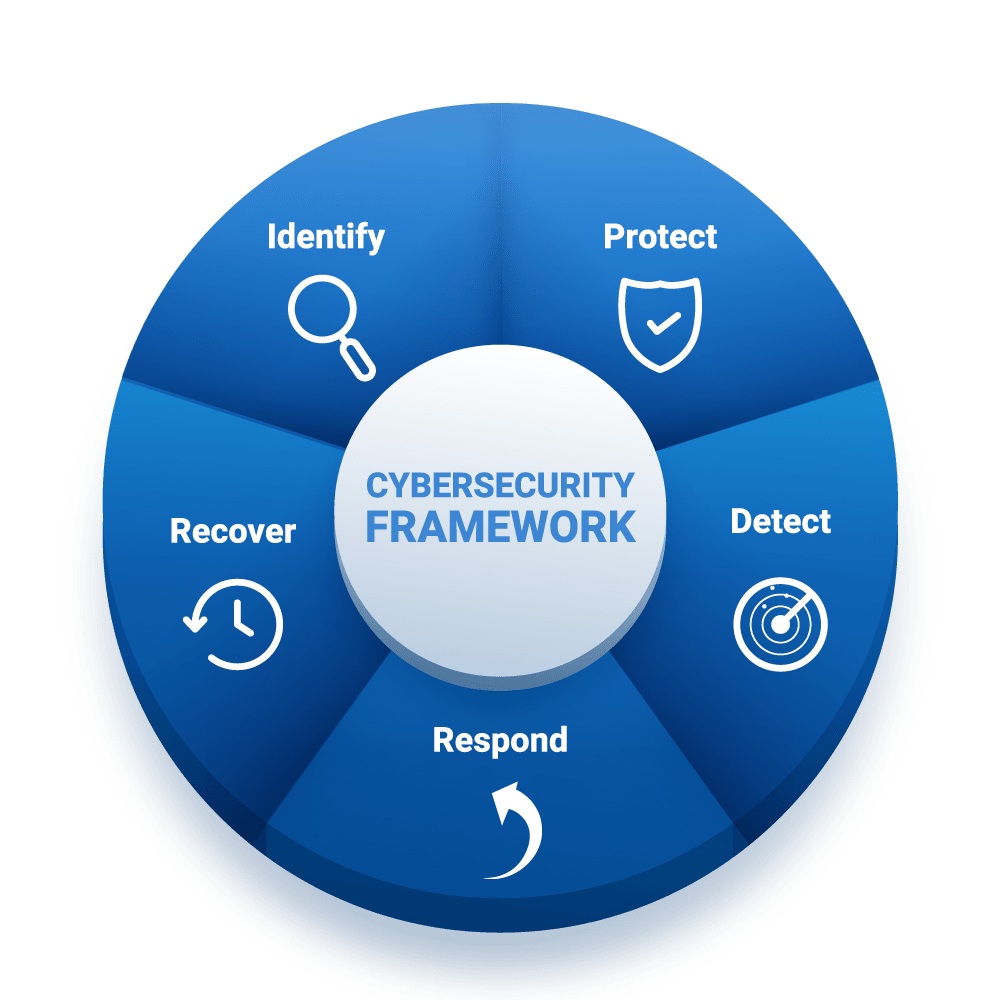
Cybersecurity
Cybersecurity can be described as the practice of protecting systems, networks, and programs from digital attacks. These cybercrime activities are either targeting or uses a computer, a computer network or a networked device. Implementing effective cybersecurity measures is particularly challenging today because there are more devices than people, and attackers are becoming more innovative.
We Serve a Variety of Businesses & Industries
A successful cybersecurity approach has multiple layers of protection spread across your computers, networks, programs, or data that you intend to keep safe.
